Security
Best Client Portals for Accounting and Finance
Can I use the client portal that came with my website? Or choose one of the old brands? The wrong secure client portal could cost you dearly in client retention, as well as security. We compare 11 client portals and additionally discuss 7 portal alternatives (such as DropBox) for accountants and tax practitioners.
Best Email Encryption Services for Small Business
(Updated August 20, 2024 to update links.) Can I use any free email encryption service? Make the wrong choice and you could end up with a service where resetting a password causes all your past emails to be unreadable (yes, these exist, and for good reason). Some assume that all your email recipients are on a corporate email server.

How Encyro Helps You Comply with HIPAA, GDPR, GLBA, IRS Pub. 4557, PCI-DSS ...
Encyro helps you safeguard customer data to help you meet many privacy and security regulations and guidelines. This article shows you how Encyro helps you meet your compliance requirements for HIPAA, GDPR, GLBA, IRS 4557, PCI-DSS and other standards.
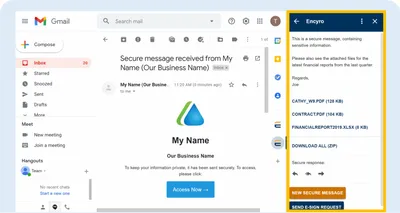
Use Encyro from Gmail
Install the Encyro addon for Gmail and read incoming secure messages or uploads directly from within Gmail. You may also download files and securely reply, reply-all, or forward a secure message. The addon also lets you send secure messages and electronic signature requests from within Gmail.

Convenience Plus Security
Email is convenient. You do not need to create an account for your client or recipient - they already have an email address. But email is not secure. Client portals are secure. But a hassle to convince the client to sign up. How can we get the best of both worlds?

Export Contacts: Make it Easy to Send Secure to Any Email Contact
Want to know the easiest way to send secure messages to any contact in your email account? You probably have a bunch of contacts who you have been emailing. Learn how to import all those contacts to your Encyro account and make sending secure messages even easier.
How to force Windows 10 to lock itself after inactivity, for all users
One of the aspects of securing your computers is to ensure that it locks itself after a period of inactivity. So, if the PC is idle, which means the user has likely left it unattended for a while, we want the screen to be locked. These instructions show you how.

How to Turn on BitLocker in Windows 10
If your PC computer is lost or stolen, having a password does not protect your data. The thief need not even login to your computer - they can simply remove the hard drive and connect it to a different computer. However, if the data is encrypted, it is practically impossible for the thief to retrieve your sensitive files. Learn how to turn on encryption.

How accountants are getting secure document portals for free!
Santa Cruz, CA accounting firm Chiorini, Hunt, and Jacobs recently had their email hacked. The hacked account contained client W2s, tax returns, social security numbers and other personal information. This loss could have easily been prevented, and for free!

Still Emailing Client Data, after GDPR?
The General Data Protection Regulation (GDPR) requires you to keep your business data secure, be it data from your clients, patients, or customers. Not just when the data is with you but also when you must pass on this data to other services, such as communicating it over email. GDPR Article 32 requires implementing technical measures to ensure data security. Find out how you can meet those requirements.

Who Uses Encyro
A review of our recent users shows that people across the United States have been active on the Encyro website. The map below shows user locations and volumes (larger circles represent more users). For privacy reasons, locations are approximate and based on IP address only; we do not link these locations to street addresses or personally identifiable information.

Why is Email Not Secure?
Your bank never emails your statement, right? Because email is not secure. Email data can be stolen as it travels un-encrypted over the network and could be stored un-encrypted on mail servers, Internet mail relays, as well as end devices. Stolen data is sold on the dark web and used to obtain loans, claim tax refunds in your name, make purchases, open new accounts, or even used to create a fake identity for illegal activities.

Easy to Receive from Clients Without Asking Them to Sign Up
Watch this 1-minute video to learn how. If your clients send you sensitive documents over email, that puts not only your client's data, but also your business, at risk. So Encyro lets you receive messages or files securely from clients, without requiring your clients to sign up for any new accounts.

Easy for You to Send, Easy for Them to Receive
When choosing an encrypted email service, it is important to consider not only how easy it is for you, but how easy (or hard) it would be for your clients to receive your secure messages. Watch this short video to see how sending and receiving works with Encyro.
How to Manage a Data Breach Incident
Last year’s big Facebook data breach sent millions of users in a flurry to reset their Facebook passwords, hoping and praying that their information hadn't found its way into the wrong hands. Some 50 million Facebook accounts were compromised. What can you do to be prepared?

Three Ways to Encrypt Email in Outlook: Comparison and Setup Instructions
Did you know that the Microsoft Outlook desktop application offers three methods to encrypt emails, including the latest Purview (OME) option that does not require installing certificates and lets you send encrypted email to external recipients? Which email encryption options are available in your scenario and which one should you choose?

12 Mistakes to Avoid When Encrypting Email in Outlook
Using the wrong Outlook plugin to encrypt your secure messages could frustrate your clients, waste your time, and even leave sensitive data saved in insecure locations. The following pitfalls are easy to avoid if you select the correct email encryption option for Microsoft Outlook.

Difference Between Identity Theft and Data Breach
Identity theft refers to stealing your personal identification information such as your social security number and other details. Data breach (also known as data loss, data leak, or data spill) on the other hand refers to stealing other people's (e.g., your clients) personal information that they shared with you. The biggest difference is that a data breach is much more sinister than identity theft in terms of damages inflicted on the victim.

5 Ways to Encrypt Email For Your Business
Choosing the wrong email encryption could shoo away clients by introducing unnecessary friction. And you may be paying for something that is not as good when the best solution is actually free. Each encryption service possesses different pros and cons, suited to different situations or businesses.

Digital Safeguards for Device Security
Digital data offers tremendous convenience and cost efficiency. From a security perspective, in many ways protecting digital data is easier as well. For instance, protecting digital data against fire or water leaks is so much more practical through an off-site backup, than maintaining photocopies of physical documents. But you do need to keep your computers and mobile devices secure. Check if have taken all these important steps.

Digital Safeguards Communications
Data leaves your device and enters the network when you explicitly send or receive documents or messages to or from your clients, vendors or others. Data also leaves your device when you enter customer data on a website (e.g. using an online service). Data is at risk whenever it leaves your device. Learn how to protect it as it travels across the network.

How To Encrypt Your WiFi Network
Data traveling over a network can often be read (snooped, eavesdropped) by unauthorized parties. Wireless networks are especially vulnerable since no physical connection to your network is needed. Someone can simply steal data as it travels over radio waves through the air.




