Digital Safeguards for Device Security

Digital data offers tremendous convenience and cost efficiency. From a security perspective, in many ways protecting digital data is easier as well. For instance, protecting digital data against fire or water leaks is so much more practical through an off-site backup, than maintaining photocopies of physical documents.
However, digital security can also introduce complexities. This article discusses protecting data stored on your computers and devices (protecting data outside your own devices, such as when it travels across the network or when it is stored in the cloud is covered in this article).
The most essential device safeguards fall into three categories:
- Access Control
- Encryption
- Malware protection
We discuss each of these below.
Device Access Control
Access control is designed to prevent unauthorized persons from logging in to one your business computers. It typically relies on using password controlled user accounts. The following best practices help ensure that your account logins are secure.
Passwords
Always enable computer accounts with passwords. Use standard accounts, and reserve administrative accounts only for users who require them.
Enforce strong passwords. To require strong passwords for all users, on each of your computers, follow the following steps with an administrator account.
Press the Windows key and “R” key simultaneously. In the little popup window towards bottom left, type “secpol.msc” without the quotes. Click OK.
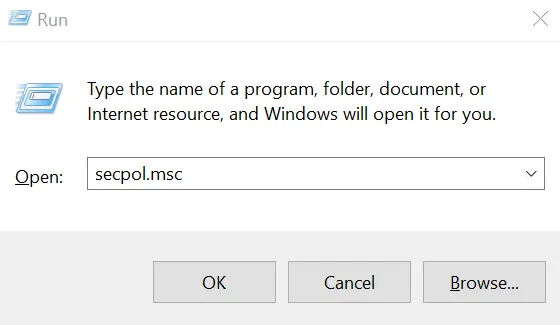
In the window that opens, double click Account Policies and then Password Policy. You will see several password related settings in the right pane.
- Make sure that “Store passwords using reversible encryption” is Disabled. By default, passwords are stored with non-reversible encryption, so that someone who steals the password file cannot get the actual passwords. Storing them with reversible encryption is almost
- Then double click “Password must meet complexity requirements” and set it to enabled.
- Optionally, you may also set “Minimum Password length” to ensure long passwords are used and “Maximum password age” to ensure passwords are changed regularly. Also, if setting the maximum password age, it makes sense to set the “Enforce password history” setting to at least 3 to ensure that the previous 3 passwords are not used.
No Guest Accounts: Make sure no guest accounts are enabled. This ensures that an unauthorized person, who happens to be near the computer, cannot just browse the computer for sensitive data and copy it to a USB stick or other removable storage device. Lack of guest accounts provides a first level defense against an unauthorized person accessing the USB ports or other attachments to introduce malware into your system.
Fortunately in Windows 10, there are no guest accounts by default.
Automatic Lockout
Set the screen to lock if left unattended for 15 minutes (or a smaller threshold duration). If you have only one user account on your PC, go to “Lock Screen” settings as follows. Type “lock Screen settings” in the search box next to the Windows start button in the lower left and click on the result titled ‘lock screen settings (system settings).’ You should arrive at a screen like so:
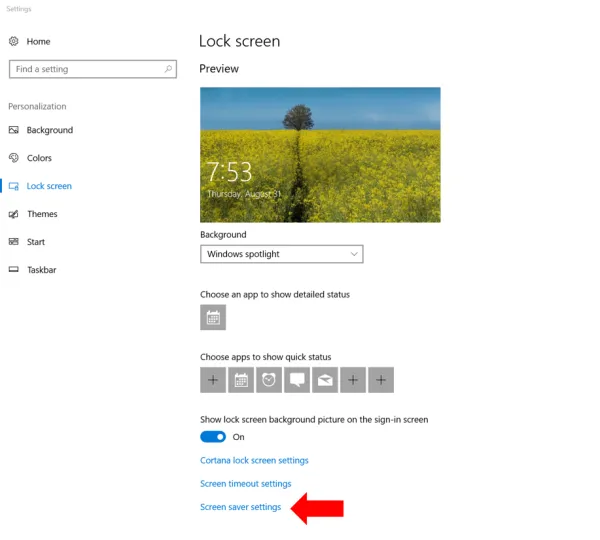
Towards the bottom, click on “Screen saver settings” and you get a popup window like so:
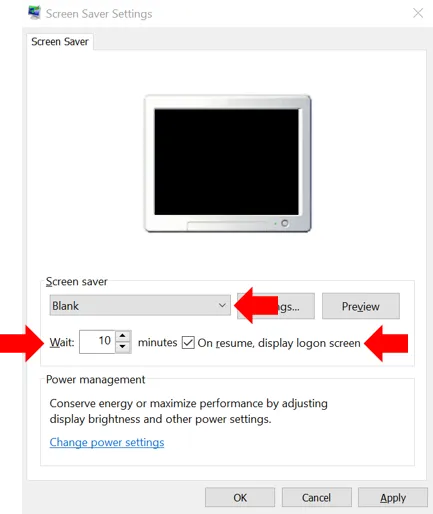
Here, in the screen saver dropdown, select the screen saver of your choice, anything other than none. Then add a checkmark next to “On resume, display logon screen.” Also make sure that the number (of minutes) after Wait is 15 or less. Click OK. Now, whenever this PC is left unattended, it will start a screen saver after the time you specified to wait. And a password will be required to resume.
If you have more than one user accounts on the PC (e.g. you have created separate accounts for your home and work related tasks, or the computer is shared with family or staff), then you need to enforce the screen timeout and lock on all users. See this article for details of how to enforce password requirement after screen timeout in Windows 10.
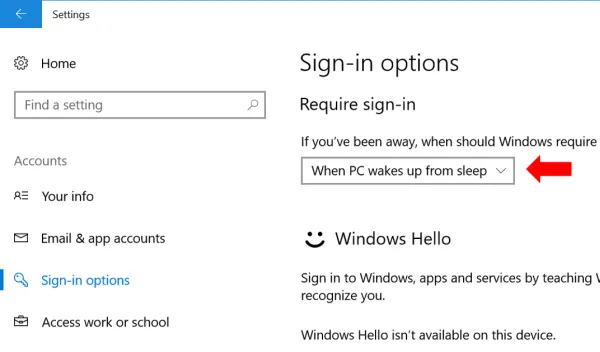
Additionally, also ensure that a password is required whenever Windows resumes from sleep or a low power mode. Go to Settings -> Accounts-> Sign in Options and under “require Sign In” make sure that When PC wakes up from sleep is selected.

Device encryption
While using computer accounts with passwords prevents casual data browsing by others, passwords do not protect the data in case the computer or its hard disk or storage media is stolen, lost, or copied. That is known as a data breach, and a practical defense is to use encryption.
Windows Computers
Microsoft provides BitLocker on Windows computers. There are two things you need to use it.
-
The right Windows version: Most Pro or Ultimate versions of Windows have BitLocker (e.g. Windows Vista and Windows 7: Enterprise and Ultimate editions; Windows 8 and 8.1: Pro and Enterprise editions; Windows 10: Pro, Enterprise, and Education editions). If you are using a Home version of Windows, it is worth considering an upgrade to the Pro version. (The cost of upgrading your OS alone should be weighed against purchasing a new PC as that will help address the second requirement below as well.)
-
The right hardware: Ideally, you need a computer with a Trusted Platform Module (TPM) chip. If you bought a business or work PC, then it likely came with a TPM. Lower priced desktops and laptops sold as ‘home use’ devices may not have a TPM. If your PC does not have a TPM, BitLocker can still be used (as described in detail below), but will require a startup password. This reduces convenience because you will need to enter an additional password every time the computer boots up. If Windows received an update overnight, the PC will not be powered up the next morning when you arrive since it will need you to enter that startup password before it can start up.
To enable BitLocker in Windows 10, open File Explorer and click on This PC.
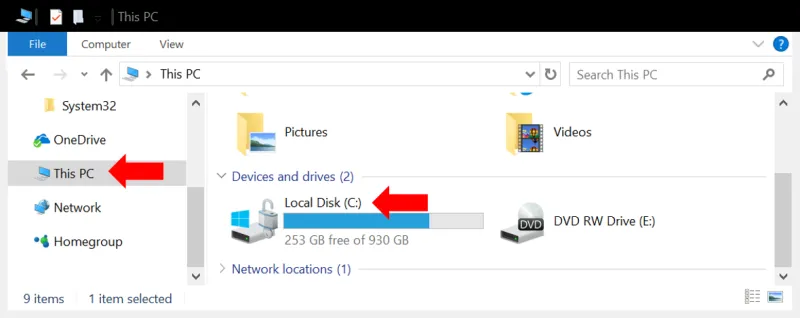
You will see all your hard drives listed. Right click on the primary drive (typically “C:”) and select Turn on BitLocker.
The turn on wizard will ask you to choose How to unlock your drive. Choose enter password. We do not recommend using a USB drive because if the USB drive is left on your desk or near your computer, it can be stolen along with the PC and then the disk is as good as not encrypted.
Recovery Key: Besides the password, Windows will provide a recovery key in case the password is forgotten (or if you used the USB drive option and the drive malfunctions). Save this recovery key somewhere away from the PC. (If the PC or its storage device and a printout of the password are stolen together, it is as good as not encrypted in the first place. That would be like leaving your house key at the front door.). A good place is to store it in your Microsoft Account online by selecting “Save to your Microsoft Account.” Alternatively, or additionally, you could also store it in your secure document portal.
For more details see instructions here, and should you want to understand all its advanced options read this, and this, more specifically for Windows 10.
Once you make your selection in the turn on BitLocker wizard, the encryption process starts. Once done, your primary drive will be encrypted. You should repeat this step on all storage drives.
If your PC does not have a TPM Chip
If your PC does not have a TPM, and you select “Turn on BitLocker,” you will get a message asking you to enable “Require additional authentication at startup.” To do this, press the Windows key and R simultaneously, to get a command window like the one below. Type the command “GPEDIT.MSC” (without quotes) and press OK.
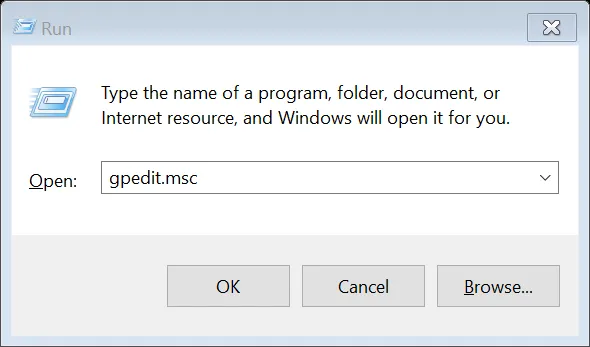
A new window called “Local Group Policy Editor” opens: go to Computer Configuration > Administrative Templates > Windows Components > Bit Locker Drive Encryption and from the expanded list click to select Operating System Devices. In the right pane, select Require additional authentication at startup.
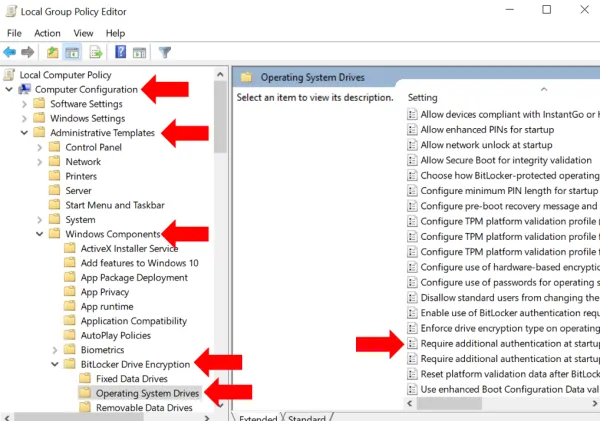
On the dialog box that opens, select Enabled and under Options, ensure that Allow Bit Locker without a compatible TPM checkbox is checked. Click OK to close the dialog and then close the Local Group Policy Editor window as well.
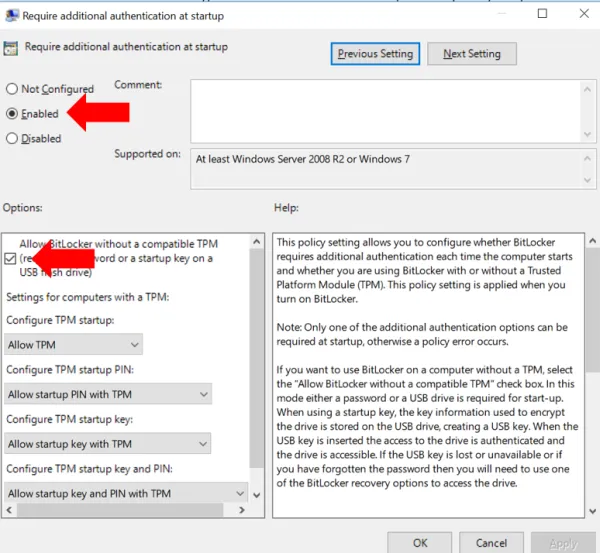
Now go back to the primary drive under This PC and again right click and Turn on BitLocker. Follow the steps described previously to save the recovery keys.
External Drives
You need to enable BitLocker on any external drives, USB disks, thumb drives and the like connected to your PC. We do not recommend using external drives to the extent possible because even after encryption, they remain difficult to track. It is not easy to ensure that every such drive is encrypted, is not accidentally decrypted, and that you know the password or recovery key for each. If you used such USB drives to move data among PCs consider using a free secure document portal to move data. If you use such a drive for backup, consider a cloud based backup service with encryption, such as CrashPlan or Carbonite. Both allow using an encryption key managed by them, or optionally known only to you.
If you must use an external disk for backup, say in addition to the cloud backup, do enable BitLocker on it. For convenience, you may set it to unlock automatically when attached to this specific computer. This way you do not need to type in the BitLocker password every time to unlock the disk. However, be aware that should you actually need to use the backup, which usually means connecting the backup drive to a different PC, you will need either the BitLocker password or recovery key. So do save them somewhere safe (in your Microsoft account or a free secure document portal).
Mac OS
Similar to BitLocker, Macs have FileVault. Its relatively easy to setup, as described here. Choose Apple menu > System Preferences, then click Security & Privacy. Click the FileVault tab. Click the Lock button, then enter an administrator name and password. Click Turn On FileVault.
This will also generate a recovery key, that helps decrypt your disk in case you forget your Mac login password or if the Mac breaks down and the disk is to be opened on another Mac. You must store this key somewhere other than on the Mac for which the key is generated. It is best not to save it near the Mac itself since in case of theft, if the thief has both the Mac and your recovery key, encryption will be useless. Apple offers to store it for you on their servers. Or, you can save it in your document portal, in a folder for yourself.
iPhones (and other iOS devices)
On iOS devices, you simply need to turn on a passcode, as explained here. Once you do that, you will see that the bottom of the Touch ID and Passcode settings screen, it says “data protection is enabled” - meaning that most of your data is encrypted (though not all data, since some apps may not be designed for security).
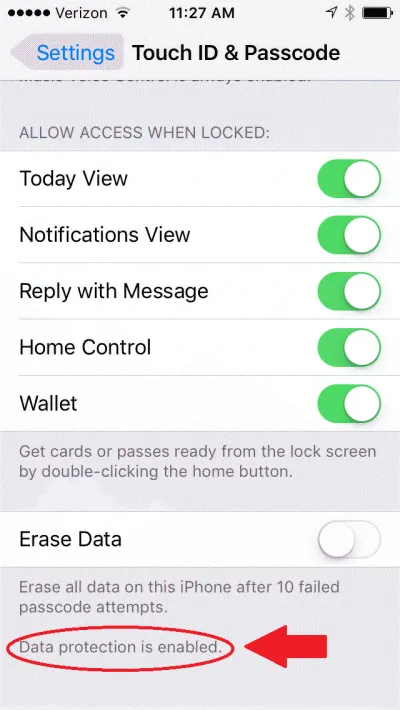
Also, make sure that remote wipe is enabled, to help erase data in case the iPhone is lost or stolen. To do this, turn on Find My iPhone as described here.
Android devices
On Android devices you need to enable the screen lock (Pattern, PIN, or Password) and require it at startup, as described here.
Any removable storage can be included for encryption by setting it up as internal storage: insert new media and tap Setup and then Use as internal storage.
Also, to enable remote wipe, turn on “Allow remote lock and erase” under Settings -> Google (or Google Settings) -> Security -> Find My Device (or Android Device Manager), as described here.

Malware protection
Malware refers to “bad” software programs that are designed by hackers to use your computer or data for their selfish purposes.
Malware includes viruses, worms, trojans, backdoors, ransomware, key-loggers, and several other types of software. Some malware may not be meant to directly harm your computer but simply use your computing resources for the hacker to run a DDoS attack on other websites. In the process, this may slow down your computer and network, or maybe end up in your computer getting disconnected from the network if the attack defenses recognize your computer as infected.
However, many types of malware more directly harm your business. They may destroy data on your computer or make it unusable. They may show annoying popups. They may establish a channel for attackers to access your computer and steal data from it at future times. They may record every keystroke you type, and hence steal all passwords or other secrets that you may not even have stored on your computer. They may steal your client list and send them emails with undesirable content.
One type of malware, Ransomware, deserves special mention because it has been growing very rapidly in the recent years. The typical attack locks up the data on your computer and ask for a payment to be made before it will release your data (paying the ransom does not guarantee that they will indeed unlock your data).
In short, malware can cause significant business loss and tarnish your reputation due to delays or data loss caused. Further, if a client realizes that your computer was the source of malware that they received, the client may lose trust in your ability to run a secure business.
How to Protect Against Malware: Protection against malware involves two components:
- preventing malware from entering your PC
- having a practical contingency plan should malware make its way in
Prevent Malware
To prevent malware from entering your computer, there are a couple of automated steps to take:
-
Keep your operating system (Windows), web browsers (IE, Chrome or whichever you use), and software up to date. Updates continually fix vulnerabilities that malware may have exploited. Use the newest operating system version - newer versions have fewer malware written for them. Most software provides settings to update itself automatically. For Windows 10, the default setting is to automatically install updates (though you can pause it temporarily under advanced settings).
-
Install an antivirus program. Windows 10 comes with Windows Defender built in. It has good protection and does not interfere with your legitimate programs. Type “Windows Defender” in the search box near the Windows Start icon and from the search results open Windows Defender Security Center. Here you can verify that malware protection is turned on and active.
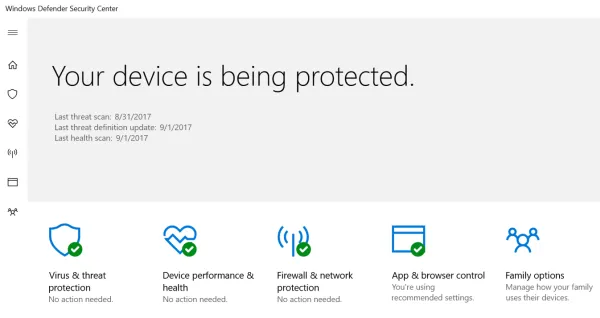
Alternatively, there are several free ones available such as Avira and Avast.
However, having the latest updates and an antivirus is not enough. Somewhat like a flu-vaccine, the anti-virus programs may prevent some viruses but not all. The second aspect is your and your team’s own security awareness. Do not click on links in emails or download attachments if the email is not from a known trusted party. Many emails pretend to be from large companies with which you likely have transacted business, and the email subject may talk about a pending order delivery, an issue with your transaction or account. Other emails may offer something enticing to make you click on a link or open an attachment. These are examples of “phishing” and you should never take their bait.
Contingency Plan
Regardless of your best intentions, malware may find its way in. That is where the contingency plan comes in. The three steps to prepare for an attack are: backup, backup, and backup. When you have a recent backup of your machine available, you can confidently proceed to removing the malware or if necessary, wipe the computer and re-install the operating system from scratch. Or in the worst case, obtain a spare PC. Since the backup will allow you to restore all your data to the restored or new PC.
Whenever you detect malware on your computer (computer acting slow, unwanted popups, websites do not behave as expected, programs open or close unexpectedly, or another symptom), it is best to disconnect it from the network. Disconnect the wired networked cable. Turn off the WiFi network at your facility (simply turning off the WiFi settings on the infected PC may not suffice since the malware may turn it back on).
Then, using another computer or mobile device, find the instructions for your anti-virus program to run a scan and attempt to remove the malware. For instance, Windows Defender instructions are here. If such a removal attempt is not successful, you may need to completely wipe the computer by installing the operating system and removing all previous contents of the storage devices connected to the computer.
To make sure you covered all the device protection safeguards, use this free data security template. The digital safeguards worksheet within this template makes sure all the above steps are taken care.
Advanced Device Security Setup
For a more sophisticated setup, that becomes necessary if you have more than a few staff members, you would want all devices to be centrally managed such that strong passwords are enforced, encryption is enforced, antivirus is maintained centrally, and certain data protection policies can be automated. This typically requires hiring an IT pro to take care if it for you.
An advanced setup may also provide for a review of audit logs for suspicious activity such as unsuccessful login attempts, excessive logins or data transfer from a computer, or installation of unapproved programs. A mobile device management (MDM) solution is typically also considered necessary to ensure all required security policies are enforced across all mobile devices used.
